Nearly half of data breaches stem from application vulnerabilities, according to a Verizon study, doubling over the past year. At the same time, the Ponemon Institute and IBM estimate that the average data breach costs nearly $4 million, translating to a significant cost for even large businesses capable of absorbing it.
Let's look at the most common application attack vectors and how you can protect your application to reduce risk.
Nearly half of data breaches come from application vulnerabilities—how vulnerable is your application to data breaches? Share on XWhat Are the Most Common Attacks?
Cyber attacks and data breaches come in many different flavors. While it would be impossible to cover every attack vector in a single blog post (or an entire blog), there are a handful of common attacks to watch out for. By understanding and protecting against these attacks, you can dramatically reduce the odds of a data breach.
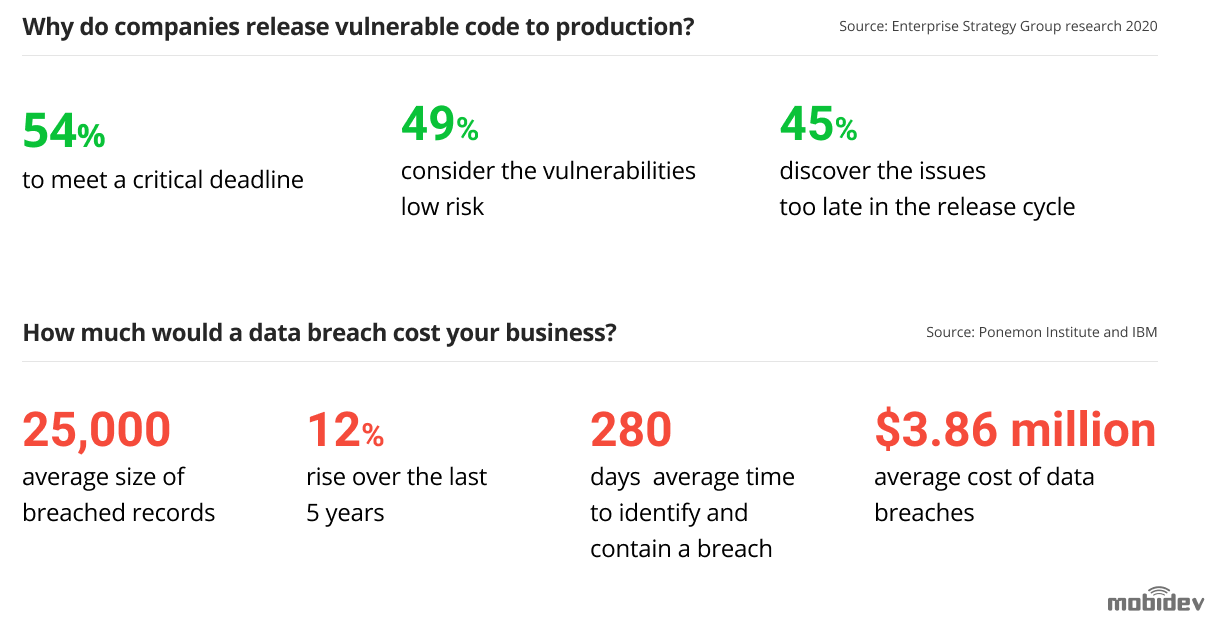
Data breaches are often an avoidable problem. Source: Mobidev
#1. SQL Injection
Most data breaches—not surprisingly—arise when hackers infiltrate a database. While there are many ways to access a database, SQL injections are the most common attack vector.
These attacks involve inserting SQL statements into web form fields. If web applications don't sanitize form input, hackers can dump the database contents to access email addresses, passwords, or other sensitive information. In other cases, they may edit content (e.g., quietly change passwords) or delete content to cause complete data loss.
#2. Cross-Site Scripting (XSS)
Other data breaches involve hackers tricking users into handing over their credentials. In many cases, these credential thefts occur via an attack vector known as cross-site scripting, or XSS.
These attacks involve compromising the interactions that users have with a vulnerable application. In particular, hackers inject malicious executable scripts (e.g., JavaScript) into a vulnerable application that executes it. The most common example is a forum where users can embed a JavaScript script in their post that other visitors inadvertently execute.
#3. Remote File Inclusion (RFI)
A similar approach to cross-site scripting is known as remote file inclusion or RFI. In these attacks, hackers cause web applications to include a remote file that executes malicious code.
The attack works when an application receives a path to a file as an input for a website and doesn't properly sanitize it. As a result, the external URL is supplied to an include function and executes on the server. While XSS affects visitors, RFI attacks server-side code, enabling hackers to steal data from an entire database.
#4. Cross-Site Request Forgery (CSRF)
Social engineering is at the heart of many data breaches. Using cross-site request forgery, or CSRF, hackers trick victims into submitting a malicious request to a web application.
These attacks often use fake websites that appear trustworthy. When a victim clicks a link or button, a GET or POST request is sent to a target web application that executes the request. If the victim is signed in to the target web application, the requests appear legitimate and execute, resulting in changed passwords, money transfers, or other actions.
#5. Dependency Vulnerabilities
Most applications make liberal use of dependencies. In fact, the average application has more than 500 open-source libraries and components! And vulnerabilities in these dependencies can create an attack vector.
Unfortunately, the number of vulnerabilities found in public repositories has sharply risen over the past few years. At the same time, component-heavy development patterns often lead to development teams that don't understand what components they use in their applications and fail to keep them out of date—exacerbating the problem.
How to Protect Your Applications
Data breaches impact even the largest companies and it's impossible to completely secure any Internet-connected application. That said, there are many best practices that you can implement across your organization to reduce the risk of a data breach, mitigate their severity, and quickly recover when a data breach does occur.
Some best practices include:
- Monitor your dependencies. GitHub's Dependabot and other tools make it easy to automatically keep dependencies up-to-date and alert you when there's a vulnerability.
- Sanitize user inputs. You can prevent most of the vulnerabilities discussed earlier by sanitizing user input. For example, PHP's filter extension makes it easy to sanitize user input with a language-level method and prevents many common attacks.
- Keep everything up-to-date. Most software applications use specific languages and frameworks that handle low-level security. By keeping these up-to-date, you can avoid any known vulnerabilities and protect against the latest attack vectors.
- Don't reinvent the wheel. Many popular frameworks include protections for things like XSS, CSRF, and RFI attacks. Rather than starting from scratch, consider using these frameworks or established open-source tools to add functionality.
- Enforce strong passwords. Require users to set strong passwords and use two-factor authentication. In addition, hash the passwords in your databases to render them useless to hackers.
- Use encryption to communicate. Force all traffic to go through SSL connections and use secure OAuth tokens for any APIs to eliminate man-in-the-middle attacks and limit potential damage.
Beyond these best practices, many organizations use Static Application Security Testing (SAST) to scan their source code for vulnerabilities as part of a continuous integration and deployment (CI/CD) process. In addition, Dynamic Application Security Testing (DAST) tools and manual penetration testing can further harden security after deployment.
In addition to these tools, many organizations use monitoring tools to observe production applications for attacks or leaks in real-time. For example, runtime application self protection (RASP) acts as a reverse proxy that observes incoming attacks and enables applications to reconfigure automatically in response to explicit conditions.
The Bottom Line
A growing number of data breaches arise from application vulnerabilities, including SQL injections, cross-site scripting, and other common attacks. Fortunately, there are a handful of best practices, actions, and software tools that you can take to harden your application and reduce the risk of a data breach.
If you need help hardening your application, Sharkbyte provides team augmentation services where our senior engineers can step in and provide insights into ways to improve.