In the first (and let's face it, the best) Matrix movie, Trinity delivers the iconic line "Dodge this" as she neutralizes another hapless Smith, downloads helicopter pilot instructions directly to her brain and takes off. It's pretty heroic stuff. Believe it or not, mobile app security is a hero’s work, too.
The truth is hackers are like real-world Smiths, and good mobile app security can stop them in their tracks. App security is a major concern as user demand for mobile apps increased each year for the past five years. According to Statista, users downloaded 230 billion mobile apps in 2021.
The truth is hackers are like real-world Smiths, and good mobile app security can stop them in their tracks. Click To TweetWhile demand growth is good news for developers, more apps also mean more user risk exposure to hackers. In a 2022 report, mobile security vendor Zimperium says the global average of hacks on mobile devices in 2021 was 23%. More bad news - the report also says that 75% of phishing sites targeted mobile devices in 2021.
The effects of a breach or attack can be severe and expensive. Companies and users may suffer financial losses if users are exposed to identity theft, fraudulent purchases, or scams.
To protect against these risks and keep customer data secure, developers must ensure their mobile applications have robust security protocols before, during, and after releasing them into the market.
Checklist of Mobile App Security Risks
A mobile app security plan should include guidelines about enforcing secure communication, providing the right permissions, storing data safely, and keeping services and dependencies updated.
In terms of functionality, mobile app security revolves around user credentials, integrity in the app, device and API channel, and API and service vulnerabilities. Let's look at some action items for a 2023 mobile app security checklist.
Audit the development team for security experience
Before you hire developers or outsource the project, be sure the development team will include some developers with security expertise. The team needs developers that will stay up-to-date with industry standards, recent breaches, and hacker threats to similar apps.
Encrypt the source code end to end
Even though open-source code is more cost-effective, it can present security risks. Make sure the code doesn't rely on algorithms or keys that could be easily compromised later. For closed-source code, be sure there is a plan to protect that code as well.
Beef up authentication
User sign-in is a tricky balance because users want secure apps that are also easy to access. App design can encourage strong passwords or incorporate biometric verification, pins, and password security questions. Aim for the highest level of authentication with minimum user friction.
Watch API permissions
Today, many apps use APIs to improve functionality, yet API permission keys can be weak points for security if hackers have access to code. For this reason, avoid hardcoding sensitive API keys into the app.
Fix unsecured data transmission
Unsecured data transmission occurs when data flows through an unsecured network connection without encryption. When hackers intercept unencrypted communication, they can view and possibly alter any data exchanged. This could allow them access to user accounts and confidential information or even take control of the device.
Data exchanged between an app and an API should be encrypted during transit with symmetric or asymmetric encryption or by using Transport Layer Security (TSL) or Secure Sockets Layer (SSL).
Data storage
Along with data in transmission, data storage is also a critical component of ensuring your app's compliance with user data regulations and overall security.
Mobile devices store data such as geolocation, personal data, correspondence, credentials, and financial data. The chart below from OWASP Mobile Top 10−2016 rating shows that data vulnerability was present in 76 percent of mobile applications.
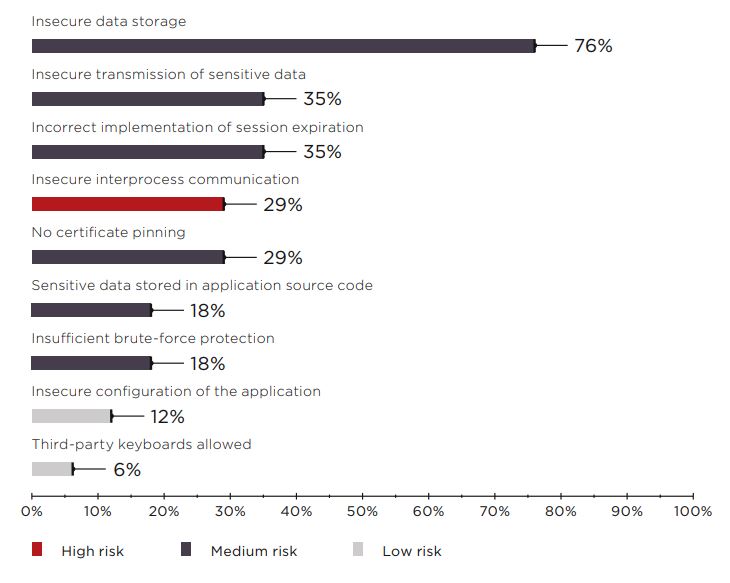
Mobile application vulnerabilities (percentage of client-side components) from Positive Technologies.
In addition to encrypting sensitive data, regular backup of encrypted databases storing sensitive information is important.
Automate wiping cached data
Mobile devices usually cache data to boost an app's performance, but this may make the app easy for attackers to breach. Hackers can decrypt the cached data to steal user data. To protect user data, set up an automated process to wipe the cached data from the app.
Routinize security where you can
Add routine security checks for the app's code to the project calendar. Regularly performing security checks is an excellent preventive step that can help avoid costly problems that would have been easier to address ahead of time. Security checks are also a good time to ensure the mobile app is still compliant with all relevant industry standards and regulations.
For example, vulnerability scanning runs automated tools to search for security flaws and vulnerabilities in applications, networks, and systems. These scans help to identify potential weaknesses that malicious actors could exploit. Organizations can regularly conduct such scans to be aware of security issues that expose their data and resources to risk.
Moving Ahead
For mobile app security, prevention is just as important as damage control. Development teams can prioritize safety from the beginning of the project and continue to monitor the app for as long as it is in the marketplace. At Sharkbyte, we have years of experience helping clients with app development, consulting, contracting, team augmentation, and even nearshore development services. Contact us today to discuss how to improve your app’s security strategy.